 Stores a generated certificate in an LDAP directory.
Stores a generated certificate in an LDAP directory.
This optional hook implementation extends and depends on the
LDAP Request Authorization hook
implementation above.
If an LDAP object was found and verified above, the certificate will
be stored in the directory in that object in an attribute specified by the
CALdapCertAttribute directive. If
an objectclass needs to be added, this is done with the
CALdapCertObjectClass directive.
If it is required that the challengePassword be used just
once, the challengePassword can be removed by specifying the
CALdapPasswordAttribute directive.
Similarly, if an objectclass needs to be removed, the objectclass can be
specified using the
CALdapPasswordObjectClass directive.
It is also possible to store the CertificateExactAssertion as described by
RFC 4523 in the same object in an attribute specified by the
CALdapPathAttribute directive. If
an objectclass needs to be added, this is done with the
CALdapPathObjectClass directive.
All of the above modifications to the directory are performed within the
same LDAP modification, and are performed as a single transaction.

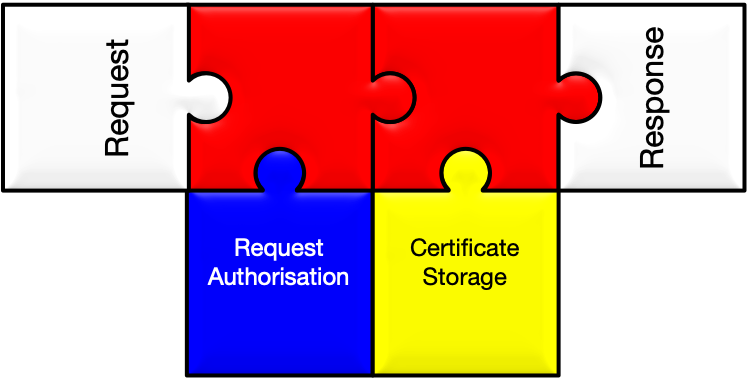
 Verifies authorization against an LDAP directory.
Verifies authorization against an LDAP directory.
 Stores a generated certificate in an LDAP directory.
Stores a generated certificate in an LDAP directory.