This module provides set of signing functions that can be used to sign certificate sign requests backed with the OpenSSL provider mechanism.
The OpenSSL provider mechanism allows access to certificates and key
described by a URI. The default URI scheme is file:,
representing the URL of a file on disk.
Based on the configuration, this module performs signing of an incoming certificate sign request using a certificate and key stored in a PEM file, on an HSM, TPM or smartcard.

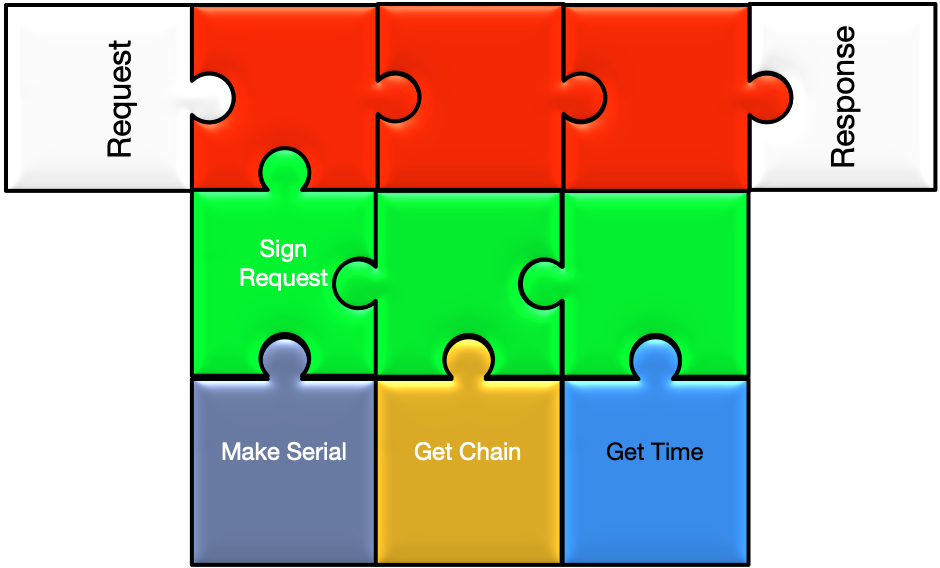
 Signs the certificate sign request using a certificate and key stored at a URI.
Signs the certificate sign request using a certificate and key stored at a URI.
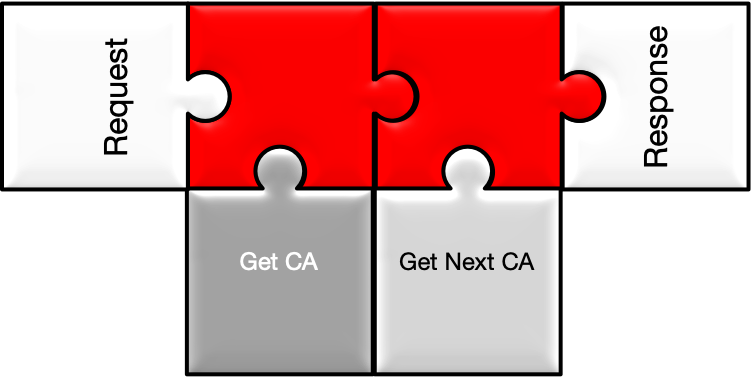
 Returns the certificate authority certificate used to sign the request.
Returns the certificate authority certificate used to sign the request.
 Returns the next certificate authority certificate that will be used to sign
future requests.
Returns the next certificate authority certificate that will be used to sign
future requests.
 Returns the chain of certificates used to sign the request.
Returns the chain of certificates used to sign the request.