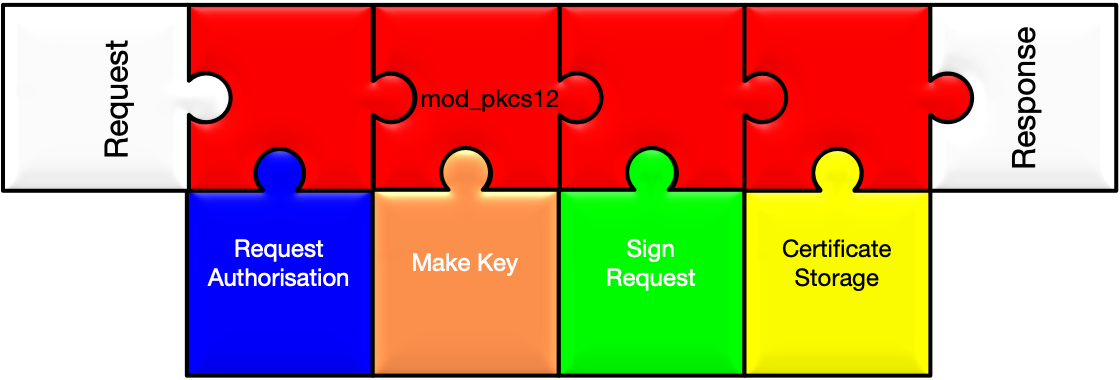
The simplest case: issue a certificate to anybody who wants one. And we trust whatever values they want to have in the 'Subject' of the certificate.
# backend configuration:
# Sign the certificates we ussue with this certificate.
# If needed - generate one for testing with:
# openssl req -new -x509 -nodes \
# -subj /CN=TheCA/O=Me/L=Here/C=EU \
# -out /etc/pki/tls/ca-cert.pem \
# -keyout /etc/pki/tls/ca-key.pem
#
CASimpleCertificate /etc/pki/tls/ca-cert.pem
CASimpleKey /etc/pki/tls/ca-key.pem
# use system clock as the time source
CASimpleTime on
# assign a random serial number
CASimpleSerialRandom on
# Specify the algorithm to use when
# generating a key; use:
#
# openssl list -public-key-algorithms
#
# to get a complete list of supported algorithms.
#
CASimpleAlgorithm RSA
Loglevel debug
<Location /pkcs12>
SetHandler pkcs12
# use subject from the certificate sign request unmodified,
# accept anything. Up to 99 'RDN' values in total.
Pkcs12SubjectRequest * 99
</Location>
Now, from a governance perspective, one generally does not allow
the user to specify everything.
So a more realistic Location block is shown below. Where
one allows the user to specify the Common Name (CN) and the Organisational
Unit (OU); but with the Organisation(O), Locality(L) and Country(C)
to forced to an appropriate value.
<Location /pkcs12>
Pkcs12SubjectRequest CN 1
Pkcs12SubjectRequest OU 1
Pkcs12SubjectSet O "Demo Services Ltd"
Pkcs12SubjectSet L "Capital City"
Pkcs12SubjectSet C "EU"
</Location>
One would normally enage with this endpoint (/pkcs12) with a some javascript from the browser or as a simple form, such as for example:
<form method=post action="/pkcs12">
Name: <input name="subject-CN" value="Alice"/>
<br/>
Department: <input name="subject-OU" value="Vermin Handling Department"/>
<br/>
Temporary password: <input name="challenge" value="s3cr!t"/>
<p/>
<input type=submit value="generate"/><br/>
</form>
Or alternatively - a curl example is shown below.
# Fetch a client certificate as a P12 for the user Alice (CN)
# with an `Organisational Unit' specified as well. The other
# fields (Country(C), Locality(L), etc) are locked down servr
# side. Curl saves this to a file (client.p12):
#
curl -o client.p12 -vvvv --silent \
--data-urlencode subject-CN=Alice \
--data-urlencode subject-OU="Vermin Handling" \
--data-urlencode challenge=s3cr1t \
http://localhost:80/pkcs12
# Decode the PKCS12 file into a PEM cert/key; using the
# challenge to decrypt the outer package.
#
openssl pkcs12 -password pass:s3cr!t -nodes -nokeys -out client.pem
# And show what is in the PEM file:
#
openssl x509 -text -noout iin client.pem