| Description |
Certificate extension to add to the certificate when signed. |
| Syntax |
CAEngineExtension string
|
| Default |
none
|
| Context |
server config, virtual host, directory, .htaccess |
| Status |
Backend
|
| Module |
mod_ca_engine |
| Compatibility |
Introduced in mod_ca 0.2.0 and works with Apache HTTP
Server 2.4.0 and later |
Certificate extension to add to the certificate when signed.
Examples of certificate extensions include:
# backend configuration:
<IfModule mod_ca_engine.c>
CAEngineExtension basicConstraints CA:FALSE
CAEngineExtension keyUsage critical,nonRepudiation,digitalSignature,keyEncipherment
CAEngineExtension extendedKeyUsage OID:1.3.6.1.5.5.7.3.2
CAEngineExtension subjectKeyIdentifier hash
CAEngineExtension authorityKeyIdentifier keyid,issuer
</IfModule>

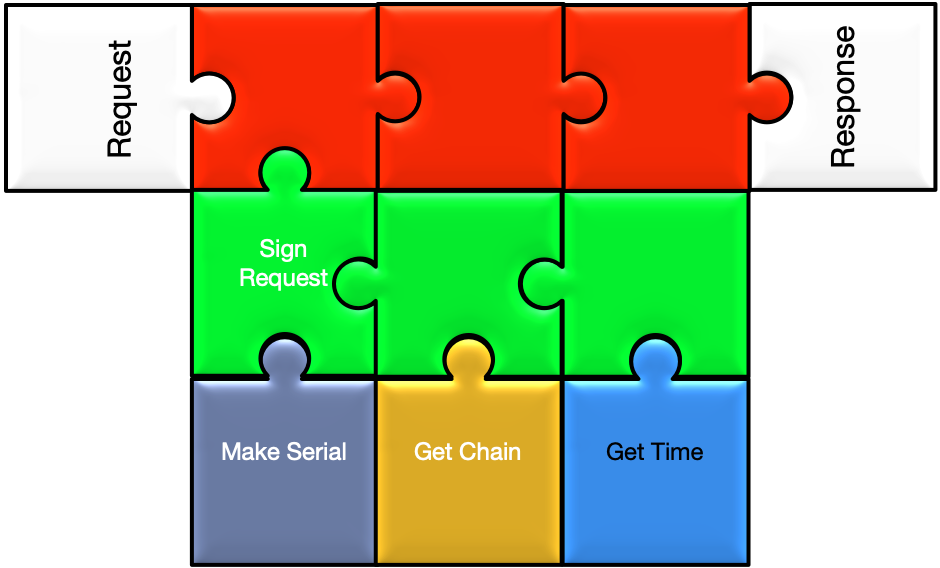
 Signs the certificate sign request using a key stored on an HSM or smartcard.
Signs the certificate sign request using a key stored on an HSM or smartcard.
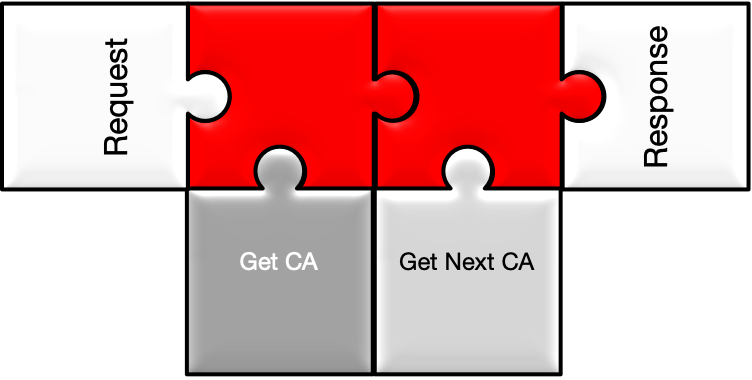
 Returns the certificate authority certificate used to sign the request.
Returns the certificate authority certificate used to sign the request.
 Returns the next certificate authority certificate that will be used to sign
future requests.
Returns the next certificate authority certificate that will be used to sign
future requests.
 Returns the chain of certificates used to sign the request.
Returns the chain of certificates used to sign the request.