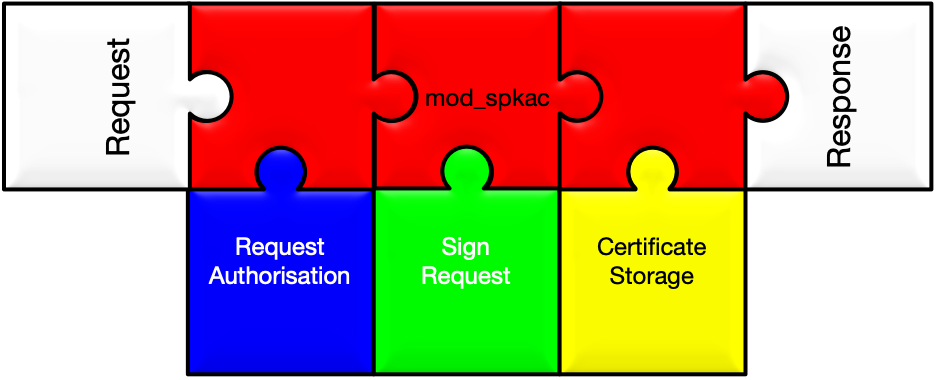
This module implements a Signed Public Key and Challenge endpoint that is capable of signing and issuing certificates on behalf of a suitable client.
Based on configuration, parameters can be passed from optional form parameters, or explicit expressions, and a new certificate sign request with acceptable parameters is combined with the public key and the challenge from the SPKAC parameter and passed to suitably configured backend modules for request authorisation, certificate signing and issuing, and certificate storage.
This module can be configured to respond to SPKAC client requests as implemented by conformant implementations of HTML5.2 and earlier.